Grype : Vulnerability Scanner for container images and file systems
Posted in Recipe on September 12, 2022 by Venkatesh S ‐ 3 min read

I have looked at at various vulnerability scanners to scan the container images and file systems. I feel that Grype is the simplest one I have seen. You don’t need to be an expert to understand perform these scans. Just run the tool on your local machine with a simple command, integrate it as a part of your CI cycle or run it again on another container, it does its job very neatly. You also get a neat report pointing out all the vulnerabilities. One tool does it all.
As the documentation says, “Grype is a vulnerability scanner for container images and file systems. Works with Syft, the powerful SBOM (software bill of materials) tool for container images and file systems.”
Find vulnerabilities for major operating system packages:
- Alpine
- Amazon Linux
- BusyBox
- CentOS
- Debian
- Distroless
- Oracle Linux
- Red Hat (RHEL)
- Ubuntu
Find vulnerabilities for language-specific packages:
- Ruby (Gems)
- Java (JAR, WAR, EAR, JPI, HPI)
- JavaScript (NPM, Yarn)
- Python (Egg, Wheel, Poetry, requirements.txt/setup.py files)
- Dotnet (deps.json)
- Golang (go.mod)
- PHP (Composer)
- Rust (Cargo)
As taken from their website, “When Grype performs a scan for vulnerabilities, it does so using a vulnerability database that’s stored on your local filesystem, which is constructed by pulling data from a variety of publicly available vulnerability data sources”. These sources include:
- Alpine Linux SecDB: https://secdb.alpinelinux.org/
- Amazon Linux ALAS: https://alas.aws.amazon.com/AL2/alas.rss
- RedHat RHSAs: https://www.redhat.com/security/data/oval/
- Debian Linux CVE Tracker: https://security-tracker.debian.org/tracker/data/json
- Github GHSAs: https://github.com/advisories
- National Vulnerability Database (NVD): https://nvd.nist.gov/vuln/data-feeds
- Oracle Linux OVAL: https://linux.oracle.com/security/oval/
- RedHat Linux Security Data: https://access.redhat.com/hydra/rest/securitydata/
- Suse Linux OVAL: https://ftp.suse.com/pub/projects/security/oval/
- Ubuntu Linux Security: https://people.canonical.com/~ubuntu-security/
Now lets see how to use this tool.
Installation
While there are various modes to install gyrpe, the simplest one is this one line command. Works on all mac and linux operating systems.
curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh -s -- -b /usr/local/bin
Running the scanner
This is the simplest part. Just one command. You can scan containers or file systems.
# scan image from the docker hub repo
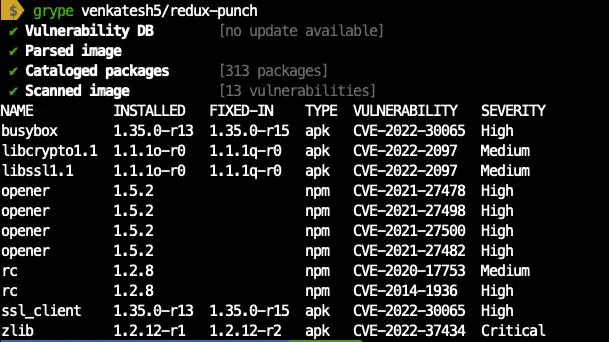
grype venkatesh5/redux-punch
# this is the general format
grype <image>
# scan a Singularity Image Format (SIF) container
syft path/to/image.sif
# scan a directory
grype dir:path/to/dir

Reporting
You can see the vulnerabilities on the screen as soon as you run the command.
You can also see a json report of the following format
{
"vulnerability": {
...
},
"relatedVulnerabilities": [
...
],
"matchDetails": [
...
],
"artifact": {
...
}
Vulnerability: All information on the specific vulnerability that was directly matched on (e.g. ID, severity, CVSS score, fix information, links for more information)
RelatedVulnerabilities: Information pertaining to vulnerabilities found to be related to the main reported vulnerability. Maybe the vulnerability we matched on was a GitHub Security Advisory, which has an upstream CVE (in the authoritative national vulnerability database). In these cases we list the upstream vulnerabilities here.
MatchDetails: This section tries to explain what we searched for while looking for a match and exactly what details on the package and vulnerability that lead to a match.
Artifact: This is a subset of the information that we know about the package (when compared to the Syft json output, we summarize the metadata section). This has information about where within the container image or directory we found the package, what kind of package it is, licensing info, pURLs, CPEs, etc.


